Protect what matters most: your industrial process
We design comprehensive strategies for physical safety and OT cybersecurity, meeting the highest industry standards.
What risks are you unknowingly taking on?
We protect industry from a global perspective
We integrate process safety, machinery protection and industrial cybersecurity into a unified approach.
We assess everything from SCADA systems, PLCs, drives, field equipment and industrial networks to process logic and the physical integrity of your assets. We apply international standards (IEC 62443, NIS2, ISO 27001), conduct penetration tests and design custom cybersecurity strategies.
We don’t just meet compliance—we enhance resilience, connecting digital and physical safety to fully protect your plant.

- OT audits
- Industrial risk assessment
- Safety standards
- OT security network
- Incident response
Industrial Safety
We design safe, efficient, and compliant industrial environments, integrating safety from the design phase to operation.
We assess and control critical processes
Using HAZOP, LOPA and functional safety studies (PL/SIL)
Industrial machine safety
We manage CE marking, applying standards such as Machinery Directive 2030/1230, ISO 13849, IEC 61508, RD1215, and others.
We integrate functional safety during the design phase
We support your design teams to incorporate safety early into processes, equipment, and control systems.
We design safety solutions that don’t slow you down
We collaborate with your team to apply safety from the engineering stage, avoiding bottlenecks and maximizing equipment availability.
The earlier safety is integrated, the lower the cost of correcting errors or adapting equipment later on.
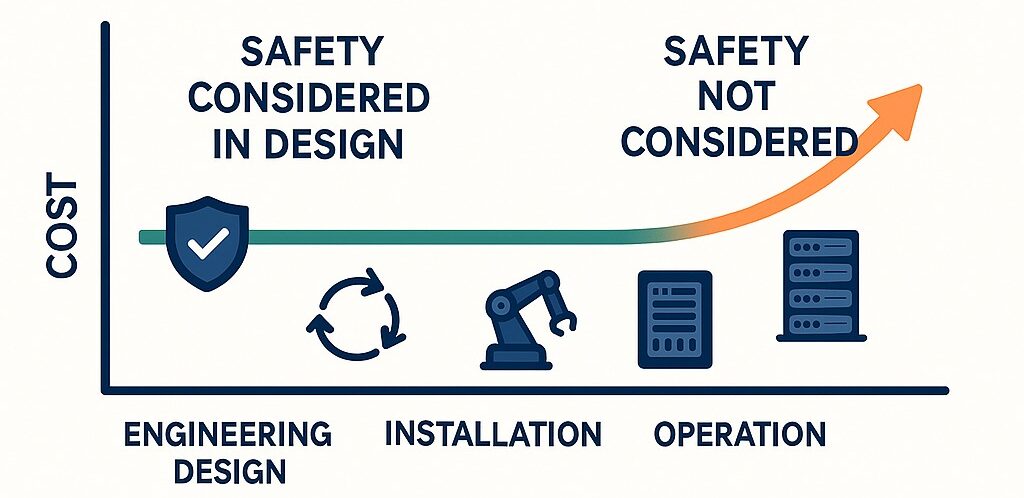
The difference lies in the process: HAZID, HAZOP, and LOPA as a foundation for safe and effective decisions
HAZID – Identificación de Peligros
HAZID is a key tool for risk analysis in industrial processes. It is used in the early stages of plant design or modification to detect potential hazards affecting people, the environment, or assets.
What makes our approach unique is that we don’t just list risks—we study the entire process, its flow, interactions, and vulnerabilities.
We also consider external factors like abnormal operating conditions, organizational changes or extreme weather.
We run structured sessions with expert participation to identify hidden vulnerabilities. A well-structured HAZID from the beginning leads to safer, more efficient design decisions and long-term cost savings.
HAZOP– Análisis de Riesgo de Procesos
HAZOP helps identify potential hazards and operational issues in complex systems, especially in chemical and industrial processes.
We analyze each process node systematically (e.g. pressure, flow, temperature), but we go beyond ticking boxes—we understand the real process.
For us, every valve has a logic, every variable a purpose. We study every deviation with cause and consequence to generate real, practical, and tailored improvements.
The result is not just a report, but a roadmap for continuous improvement and risk prevention.
HAZOP Methodology Advantages:
LOPA - Layer of Protection Analysis
LOPA evaluates whether the existing protection layers in a plant are enough to reduce risk to an acceptable level.
It is an intermediate tool between qualitative and quantitative risk analysis, focusing on the probability of failure and barrier effectiveness.
We don’t add safety layers just to check boxes—we assess how alarms, SIS, or human intervention fit into the sequence of events.
We analyze each scenario’s root cause, frequency, and consequences to decide if protections are enough or if upgrades are needed.
LOPA allows us to justify design, investment and operational decisions objectively, ensuring risks are under control.
We understand machinery safety is not just legal compliance—it ensures safe workplaces, efficient processes, and uninterrupted operation.
We evaluate risks and apply standards like 2006/42/EC, ISO 13849, IEC 62061, across the entire machine lifecycle: design, integration, operation, and maintenance.
We help you:
Identify hazards and critical points
Evaluate and reduce risks per regulations
Validate hardware/software safety systems
Ensure CE compliance and documentation
Integrate safety without losing efficiency
We connect physical machine safety with OT cybersecurity, for end-to-end protection—from sensor to network.
Ciberseguridad OT
We protect your industrial systems from digital and regulatory threats, integrating cybersecurity into your operations and compliance strategy.
We assess and reinforce your OT systems’ security. We conduct technical audits, penetration tests (pentests), and vulnerability assessments in real industrial environments.
We translate regulations into actionable measures. We apply frameworks like NIS2, CRA, IEC 62443, GDPR, the Data Act, or the Artificial Intelligence Act, adapting them to your OT processes and operational reality.
We classify risks and roles in the value chain. We define whether your organization acts as a provider, integrator, or end user—and what each role implies in terms of regulatory responsibilities.
We train your teams and prepare you for what’s coming. We provide internal training and technical documentation to support future compliance without disrupting your current activity.
While Operational Technology (OT) systems use tools similar to those of Information Technology (IT), their objectives are different.
IT cybersecurity focuses on the confidentiality, integrity, and availability of data, whereas OT cybersecurity prioritizes operational continuity, physical safety, and real-time availability of industrial processes.
OT devices—such as PLCs, sensors, actuators, and SCADA systems—are designed to control physical equipment. These environments often have longer life cycles, limited tolerance for interruptions, and legacy technologies that are hard to update, making them especially vulnerable.
Applying OT cybersecurity strategies isn’t about replicating IT solutions—it’s about adapting them to a completely different operational ecosystem
| Aspect | IT (Information Technology) | OT (Operational Technology) |
|---|---|---|
| Main objective | Protect the confidentiality, integrity, and availability of data. | Ensure operational continuity and safety of physical processes. |
| Interaction | User ↔ Software ↔ Data | Machine ↔ Machine (M2M) and control of physical equipment |
| Types of assets | Servers, networks, PCs, applications, databases | PLCs, sensors, actuators, HMI, SCADA, DCS |
| Impact of an attack | Data loss, reputational damage, information leakage | Plant shutdowns, physical damage, risk to people or facilities |
| Interruption tolerance | High: reboots or patches can be scheduled without critical risk | Minimal: even short downtimes may compromise safety or production |
| Updates and patches | Frequent and easily scheduled | Limited, due to process impact or compatibility issues |
| System lifecycle | Short: 3–5 years | Long: 10–30 years, often with legacy systems |
| Applicable standards | ISO 27001, NIST, GDPR | IEC 62443, NIST 800-82, ISA-99 |
For years, Information Technology (IT) and Operational Technology (OT) evolved separately. IT focused on data and corporate systems, while OT focused on physical control and continuous uptime.
With the rise of the Industrial Internet of Things (IIoT), this separation has narrowed. Smart sensors, connected systems, and data platforms now enable real-time monitoring of industrial operations. This has improved efficiency and decision-making—but has also exposed OT environments to new external threats.
Protecting these environments requires an adapted OT and industrial IoT cybersecurity strategy that understands real-time criticality, long life cycles, and the impossibility of stopping systems for updates.
How do we work?
-
Plant diagnosis
Technical analysis and interviews to understand your operational reality.
-
Vulnerability detection
OT evaluation and compliance, using specialized tools.
-
Personalized action plan
Roadmap with concrete measures, priorities, and expected return.
-
Monitoring and evolution
Continuous support and periodic review of maturity level.
Ready to protect your industrial plant comprehensively?
Free, no-obligation diagnosis in less than 4 hours.
